Windows Blocking Network Traffic Capture
Categories:
- Windows Blocking Network Traffic Capture
Windows Blocking Network Traffic Capture
- Windows Blocking Network Traffic Capture
- Need to identify blocked traffic, including outbound and inbound.
- Two ways of blocking: by connection or by packet. Packet drops occur frequently and the reason must be audited; connection‐oriented blocks align better with real-world monitoring.
- Many normally processed packets may also be dropped, so we must distinguish drops from actual blocks—we focus on blocks.
Setting Up a Test Project
WFP mainly runs in user mode and partly in kernel mode, exposed as drivers. The test setup is complex.
Recommended: run a separate physical machine for testing, compile on the dev box, then copy and remotely debug on the test machine.
For those with limited resources, local debugging on the same machine is also possible.
- Microsoft WFP Sample Project
- Focus only on: Windows-driver-samples\network\trans\WFPSampler
- WFPSampler Guide
Build Issues:
Other Issues:
Capturing Block Events via Auditing
By default, auditing for WFP is off.
- Audit can be enabled by category (via Group Policy Object Editor MMC, Local Security Policy MMC, or auditpol.exe).
- Audit can also be enabled by subcategory with auditpol.exe.
- Always use GUIDs—otherwise localized display strings break cross-language systems.
- Audit uses circular logs of 128 KB—low resource impact.
Categories https://docs.microsoft.com/en-us/windows/win32/secauthz/auditing-constants
| Category/Subcategory | GUID |
|---|---|
| … | … |
| Object Access | {6997984A-797A-11D9-BED3-505054503030} |
| Policy Change | {6997984D-797A-11D9-BED3-505054503030} |
| … | … |
Object Access subcategories and their GUIDs https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-gpac/77878370-0712-47cd-997d-b07053429f6d
| Object Access Subcategory | Subcategory GUID | Inclusion Setting |
|---|---|---|
| … | … | … |
| Filtering Platform Packet Drop | {0CCE9225-69AE-11D9-BED3-505054503030} | No Auditing |
| Filtering Platform Connection | {0CCE9226-69AE-11D9-BED3-505054503030} | No Auditing |
| Other Object Access Events | {0CCE9227-69AE-11D9-BED3-505054503030} | No Auditing |
| … | … | … |
Policy Change subcategories and GUIDs:
| Policy Change Subcategory | Subcategory GUID |
|---|---|
| Audit Policy Change | {0CCE922F-69AE-11D9-BED3-505054503030} |
| Authentication Policy Change | {0CCE9230-69AE-11D9-BED3-505054503030} |
| Authorization Policy Change | {0CCE9231-69AE-11D9-BED3-505054503030} |
| MPSSVC Rule-Level Policy Change | {0CCE9232-69AE-11D9-BED3-505054503030} |
| Filtering Platform Policy Change | {0CCE9233-69AE-11D9-BED3-505054503030} |
| Other Policy Change Events | {0CCE9234-69AE-11D9-BED3-505054503030} |
# auditpol reference: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/auditpol
# This section focuses on the 'Object Access' category
# List available fields
# -v shows GUID, -r produces CSV report
auditpol /list /category /v
auditpol /list /subcategory:* /v
# Get audit settings for a subcategory
auditpol /get /category:'Object Access' /r | ConvertFrom-Csv | Get-Member
# Query subcategory GUID
auditpol /get /category:'Object Access' /r | ConvertFrom-Csv | Format-Table Subcategory,'Subcategory GUID','Inclusion Setting'
# Lookup subcategory
auditpol /list /subcategory:"Object Access","Policy Change" -v
# Backup
auditpol /backup /file:d:\audit.bak
# Restore
auditpol /restore /file:d:\audit.bak
# Modify Policy
# **Policy Change** | {6997984D-797A-11D9-BED3-505054503030}
auditpol /set /category:"{6997984D-797A-11D9-BED3-505054503030}" /success:disable /failure:disable
# Filtering Platform Policy Change | {0CCE9233-69AE-11D9-BED3-505054503030}
auditpol /set /subcategory:"{0CCE9233-69AE-11D9-BED3-505054503030}" /success:enable /failure:enable
# **Object Access** | {6997984A-797A-11D9-BED3-505054503030}
auditpol /get /category:"{6997984A-797A-11D9-BED3-505054503030}"
auditpol /set /category:"{6997984A-797A-11D9-BED3-505054503030}" /success:disable /failure:disable
# Filtering Platform Packet Drop | {0CCE9225-69AE-11D9-BED3-505054503030}
auditpol /set /subcategory:"{0CCE9225-69AE-11D9-BED3-505054503030}" /success:disable /failure:enable
# Filtering Platform Connection | {0CCE9226-69AE-11D9-BED3-505054503030}
auditpol /set /subcategory:"{0CCE9226-69AE-11D9-BED3-505054503030}" /success:disable /failure:enable
# Read audit logs
$Events = Get-WinEvent -LogName 'Security'
foreach ($event in $Events) {
ForEach ($line in $($event.Message -split "`r`n")) {
Write-Host $event.RecordId ':' $Line
break
}
}
Event Details:
| Event ID | Explanation |
|---|---|
| 5031(F) | The Windows Firewall Service blocked an application from accepting incoming connections on the network. |
| 5150(-) | The Windows Filtering Platform blocked a packet. |
| 5151(-) | A more restrictive Windows Filtering Platform filter has blocked a packet. |
| 5152(F) | The Windows Filtering Platform blocked a packet. |
| 5153(S) | A more restrictive Windows Filtering Platform filter has blocked a packet. |
| 5154(S) | The Windows Filtering Platform has permitted an application or service to listen on a port for incoming connections. |
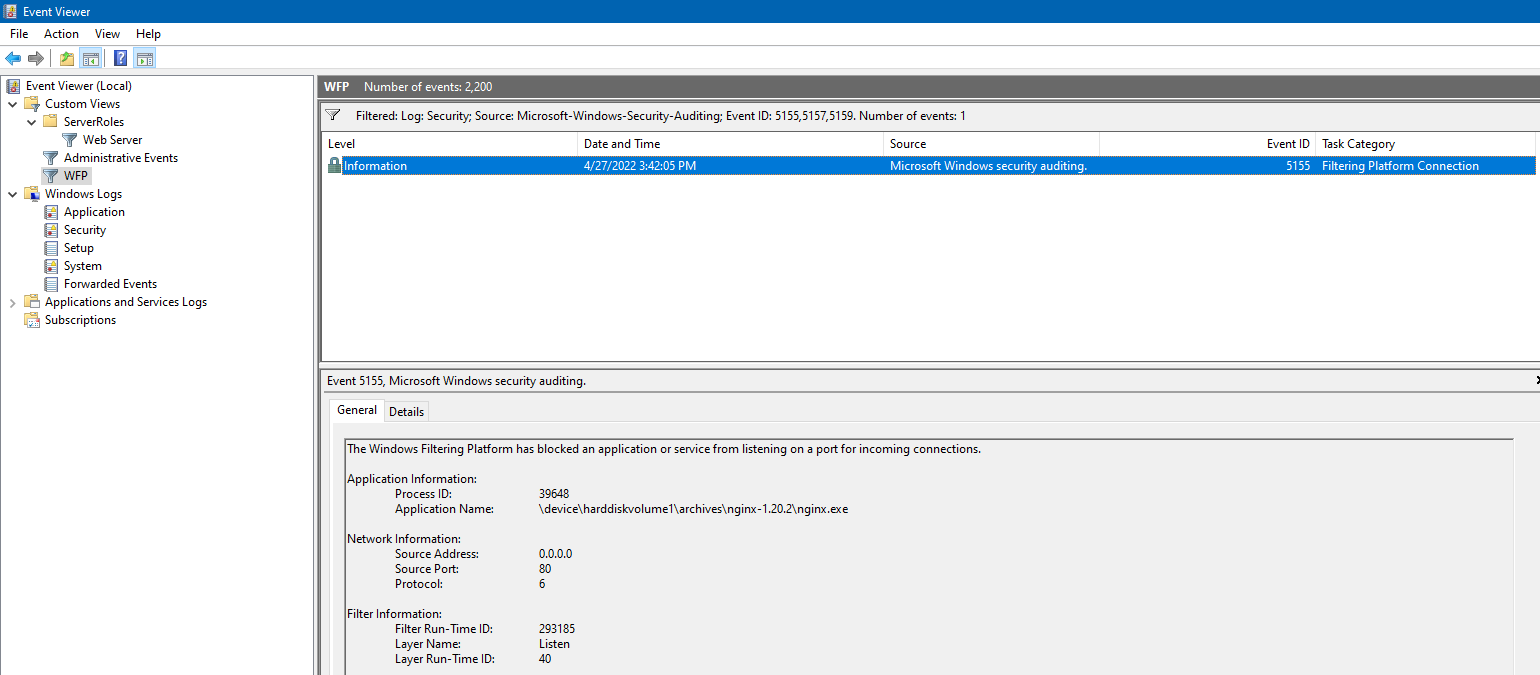
| 5155(F) | The Windows Filtering Platform has blocked an application or service from listening on a port for incoming connections. |
| 5156(S) | The Windows Filtering Platform has permitted a connection. |
| 5157(F) | The Windows Filtering Platform has blocked a connection. |
| 5158(S) | The Windows Filtering Platform has permitted a bind to a local port. |
| 5159(F) | The Windows Filtering Platform has blocked a bind to a local port. |
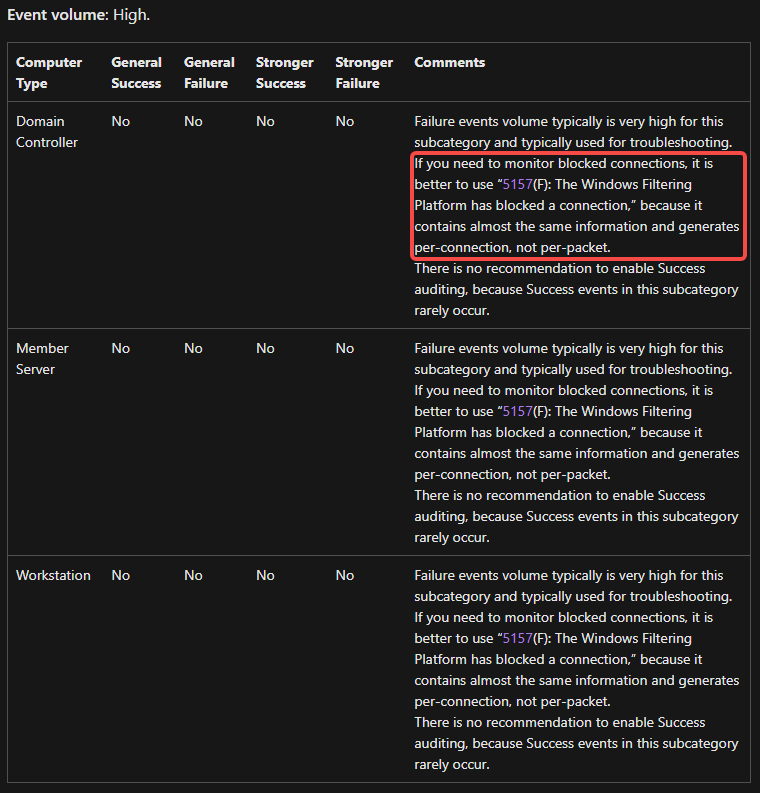
Events to Focus On:
- Audit Filtering Platform Packet Drop
-
These events generate huge volumes; focus on 5157, which records almost the same data but per-connection rather than per-packet.
-
Failure volume is typically very high for this subcategory and mainly useful for troubleshooting. To monitor blocked connections, 5157(F): The Windows Filtering Platform has blocked a connection is recommended since it contains nearly identical information and generates per-connection instead of per-packet.
-
- Audit Filtering Platform Connection
- It is best to monitor only failure events such as blocked connections; track allowed connections only when necessary.
- 5031
- If there are no firewall rules (Allow or Deny) for a specific application in Windows Firewall, traffic will be dropped at the WFP layer, which by default denies all inbound connections.
51505151- 5155
- 5157
- 5159
Obtaining Provider Information
# List security-related providers
Get-WinEvent -ListProvider "*Security*" | Select-Object ProviderName,Id
# Microsoft-Windows-Security-Auditing 54849625-5478-4994-a5ba-3e3b0328c30d
# Show tasks for a provider
Get-WinEvent -ListProvider "Microsoft-Windows-Security-Auditing" | Select-Object -ExpandProperty tasks
# SE_ADT_OBJECTACCESS_FIREWALLCONNECTION 12810 Filtering Platform Connection 00000000-0000-0000-0000-000000000000
| ProviderName | Id |
|---|---|
| Security Account Manager | 00000000-0000-0000-0000-000000000000 |
| Security | 00000000-0000-0000-0000-000000000000 |
| SecurityCenter | 00000000-0000-0000-0000-000000000000 |
| Microsoft-Windows-Security-SPP-UX-GenuineCenter-Logging | fb829150-cd7d-44c3-af5b-711a3c31cedc |
| Microsoft-Windows-Security-Mitigations | fae10392-f0af-4ac0-b8ff-9f4d920c3cdf |
| Microsoft-Windows-VerifyHardwareSecurity | f3f53c76-b06d-4f15-b412-61164a0d2b73 |
| Microsoft-Windows-SecurityMitigationsBroker | ea8cd8a5-78ff-4418-b292-aadc6a7181df |
| Microsoft-Windows-Security-Adminless | ea216962-877b-5b73-f7c5-8aef5375959e |
| Microsoft-Windows-Security-Vault | e6c92fb8-89d7-4d1f-be46-d56e59804783 |
| Microsoft-Windows-Security-Netlogon | e5ba83f6-07d0-46b1-8bc7-7e669a1d31dc |
| Microsoft-Windows-Security-SPP | e23b33b0-c8c9-472c-a5f9-f2bdfea0f156 |
| Microsoft-Windows-Windows Firewall With Advanced Security | d1bc9aff-2abf-4d71-9146-ecb2a986eb85 |
| Microsoft-Windows-Security-SPP-UX-Notifications | c4efc9bb-2570-4821-8923-1bad317d2d4b |
| Microsoft-Windows-Security-SPP-UX-GC | bbbdd6a3-f35e-449b-a471-4d830c8eda1f |
| Microsoft-Windows-Security-Kerberos | 98e6cfcb-ee0a-41e0-a57b-622d4e1b30b1 |
| Microsoft-Windows-Security-ExchangeActiveSyncProvisioning | 9249d0d0-f034-402f-a29b-92fa8853d9f3 |
| Microsoft-Windows-NetworkSecurity | 7b702970-90bc-4584-8b20-c0799086ee5a |
| Microsoft-Windows-Security-SPP-UX | 6bdadc96-673e-468c-9f5b-f382f95b2832 |
| Microsoft-Windows-Security-Auditing | 54849625-5478-4994-a5ba-3e3b0328c30d |
| Microsoft-Windows-Security-LessPrivilegedAppContainer | 45eec9e5-4a1b-5446-7ad8-a4ab1313c437 |
| Microsoft-Windows-Security-UserConsentVerifier | 40783728-8921-45d0-b231-919037b4b4fd |
| Microsoft-Windows-Security-IdentityListener | 3c6c422b-019b-4f48-b67b-f79a3fa8b4ed |
| Microsoft-Windows-Security-EnterpriseData-FileRevocationManager | 2cd58181-0bb6-463e-828a-056ff837f966 |
| Microsoft-Windows-Security-Audit-Configuration-Client | 08466062-aed4-4834-8b04-cddb414504e5 |
| Microsoft-Windows-Security-IdentityStore | 00b7e1df-b469-4c69-9c41-53a6576e3dad |
Triggering a Block Event
Warning: Creating block filters affects other software on the host!
You can immediately clean up with .\WFPSampler.exe -clean.
Steps:
-
Enable auditing for Filtering Platform Connection:
auditpol /set /subcategory:"{0CCE9226-69AE-11D9-BED3-505054503030}" /success:enable /failure:enable -
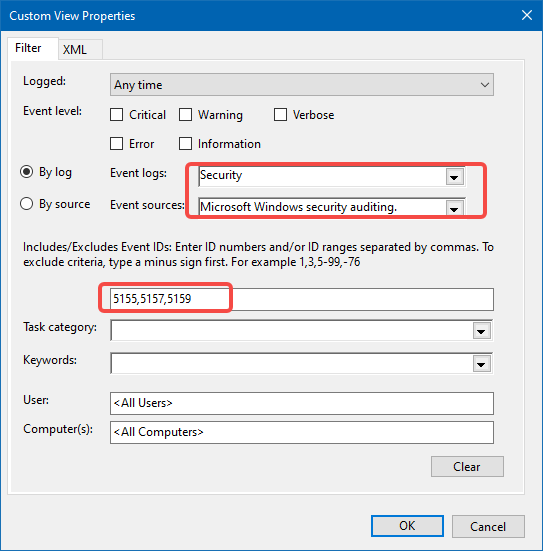
Open Event Viewer, create a Custom View/filter for IDs 5155, 5157, 5159.
-
Add a WFP filter using WFPSampler.exe to block listening on port 80:
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_LISTEN_V4 -iplp 80 -
Run a third-party (non-IIS) HTTP server—here we use nginx on port 80. Starting it triggers event 5155.
-
Clean up the filter:
.\WFPSampler.exe -clean -
Disable auditing:
auditpol /set /category:"{0CCE9226-69AE-11D9-BED3-505054503030}" /success:disable /failure:disable
# 5155: an application or service was blocked from listening on a port
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_LISTEN_V4
# 5157: a connection was blocked
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_RECV_ACCEPT_V4
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_CONNECT_V4
# 5159: binding to a local port was blocked
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_RESOURCE_ASSIGNMENT_V4
# Other
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_RESOURCE_ASSIGNMENT_V4_DISCARD
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_RECV_ACCEPT_V4_DISCARD
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_CONNECT_V4_DISCARD
# List a WFP filter by ID:
netsh wfp show filters
# Get layer IDs:
netsh wfp show state
Monitoring Network Events (NET_EVENT)
- Events support both enumeration and subscription.
- Enumeration allows filter criteria, querying events within a time window.
- Subscriptions inject a callback to deliver events in real time.
Supported event types:
typedef enum FWPM_NET_EVENT_TYPE_ {
FWPM_NET_EVENT_TYPE_IKEEXT_MM_FAILURE = 0,
FWPM_NET_EVENT_TYPE_IKEEXT_QM_FAILURE,
FWPM_NET_EVENT_TYPE_IKEEXT_EM_FAILURE,
FWPM_NET_EVENT_TYPE_CLASSIFY_DROP,
FWPM_NET_EVENT_TYPE_IPSEC_KERNEL_DROP,
FWPM_NET_EVENT_TYPE_IPSEC_DOSP_DROP,
FWPM_NET_EVENT_TYPE_CLASSIFY_ALLOW,
FWPM_NET_EVENT_TYPE_CAPABILITY_DROP,
FWPM_NET_EVENT_TYPE_CAPABILITY_ALLOW,
FWPM_NET_EVENT_TYPE_CLASSIFY_DROP_MAC,
FWPM_NET_EVENT_TYPE_LPM_PACKET_ARRIVAL,
FWPM_NET_EVENT_TYPE_MAX
} FWPM_NET_EVENT_TYPE;
Enumeration filter fields (FWPM_NET_EVENT_ENUM_TEMPLATE):
| Value | Meaning |
|---|---|
| FWPM_CONDITION_IP_PROTOCOL | The IP protocol number, as specified in RFC 1700. |
| FWPM_CONDITION_IP_LOCAL_ADDRESS | The local IP address. |
| FWPM_CONDITION_IP_REMOTE_ADDRESS | The remote IP address. |
| FWPM_CONDITION_IP_LOCAL_PORT | The local transport protocol port number. For ICMP, the message type. |
| FWPM_CONDITION_IP_REMOTE_PORT | The remote transport protocol port number. For ICMP, the message code. |
| FWPM_CONDITION_SCOPE_ID | The interface IPv6 scope identifier. Reserved for internal use. |
| FWPM_CONDITION_ALE_APP_ID | The full path of the application. |
| FWPM_CONDITION_ALE_USER_ID | The identification of the local user. |
Outside of drivers, only basic drop events are returned.
Monitoring Network Connections (NetConnection)
Compared to monitoring network events, monitoring connections requires higher privileges.
callback approach
The caller needs FWPM_ACTRL_ENUM access to the connection objects’ containers and FWPM_ACTRL_READ access to the connection objects. See Access Control for more information.
Monitoring network connections has not yet succeeded.
I found a similar issue: Receiving in/out traffic stats using WFP user-mode API. It matches the behavior I observed—none of the subscribing functions receive any notifications, giving no events and no errors. Neither enabling auditing nor elevating privileges helped. Some noted that non-kernel mode can only receive drop events, which is insufficient for obtaining block events.
Example of adding a security descriptor: https://docs.microsoft.com/en-us/windows/win32/fwp/reserving-ports
Application Layer Enforcement (ALE) Introduction
- ALE comprises a set of kernel-mode filters that support stateful filtering.
- Filters at the ALE layer can authorize connection creation, port allocation, socket management, raw socket creation, and promiscuous-mode reception.
- Classification of ALE-layer filters is based on the connection or socket; filters in other layers can only classify based on individual packets.
- ALE filter reference: ale-layers
- More filter reference: filtering-layer-identifiers
Coding Notes
Most WFP functions can be invoked from either user mode or kernel mode. However, user-mode functions return a DWORD representing a Win32 error code, whereas kernel-mode functions return an NTSTATUS representing an NT status code.
Therefore, functions share the same names and semantics across modes but have differing signatures. Separate user-mode and kernel-mode headers are required: user-mode header file names end with “u”, and kernel-mode ones end with “k”.
Conclusion
Our requirement is merely to know when events occur; real-time handling is unnecessary, and developing a kernel driver would introduce greater risk. Consequently, we’ll rely on event auditing and monitor event log generation to acquire block events.
A dedicated thread will use NotifyChangeEventLog to watch for new log records.
Appendix
WFP Architecture
WFP (Windows Filter Platform) 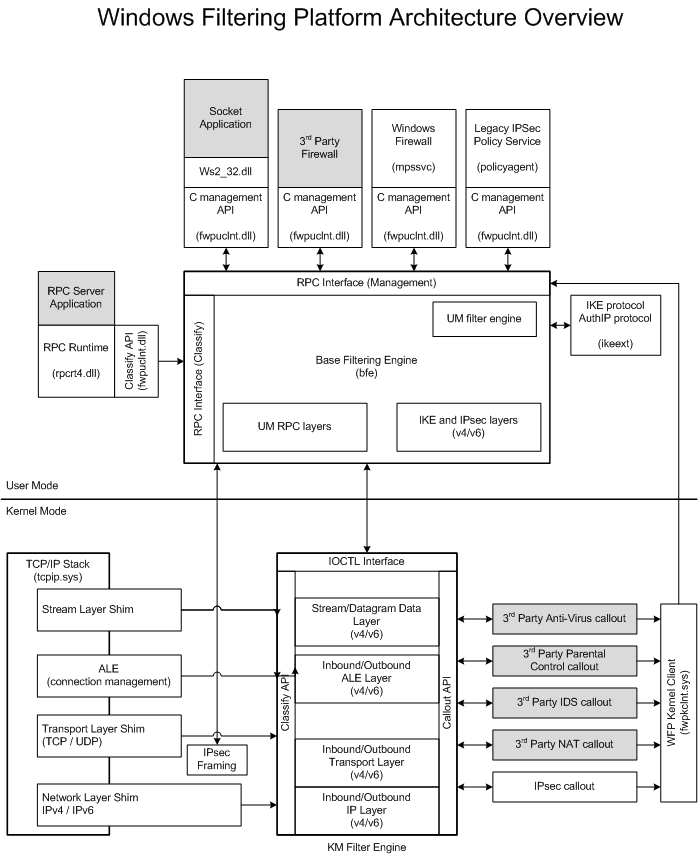
Data Flow
Data flow:
- A packet enters the network stack.
- The network stack finds and invokes a shim.
- The shim initiates classification at a particular layer.
- During classification, filters are matched, and the resulting action is applied. (See Filter Arbitration.)
- If any callout filters match, their corresponding callouts are invoked.
- The shim enforces the final filtering decision (e.g., drop the packet).