A Few Ways to Safely Use Public IPv6
Categories:
Some people need to “go home” via public IPv6. Unlike Tailscale/Zerotier et al., which rely on NAT traversal to create direct tunnels, native IPv6 offers a straight-through connection. Cellular networks almost always hand out global IPv6 addresses, so “going home” is extremely convenient.
I previously posted Using Common DDNS Sub-domains on Home Broadband May Downgrade Telecom Service describing a pitfall with IPv6: domains get crawled. Exposing your domain is basically the same as exposing your IPv6 address. Once scanners find open services and inbound sessions pile up, the ISP may silently throttle or downgrade your line.
That thread mentioned domain scanning but not cyberspace scanning—which ignores whatever breadcrumbs you leave and just brute-forces entire address blocks. This is much harder to defend against.
Cyberspace scanning usually includes the following steps:
- Host-alive detection using ARP, ICMP, or TCP to list responsive IPs.
- Port / service discovery to enumerate open ports and identify service names, versions, and OS signatures.
- Operating-system fingerprinting by analyzing packet replies.
- Traffic collection to spot anomalies or attack patterns.
- Alias resolution mapping multiple IPs to the same router.
- DNS recon reverse-resolving IPs to domain names.
Below are a few methods to stay off those scanners:
- Have your internal DNS server never return AAAA records.
- Allow internal services to be reached only via domain names, never by raw IP.
- Use a private DNS service such as AdGuardPrivate.
Prevent AAAA Records on the Internal DNS
When you browse the web, every outbound connection can leak your source IPv6. If a firewall isn’t in place, that address enters the scanners’ high-priority IP pools.
Even scanning only the last 16 bits of a /56 prefix becomes a smaller task once the prefix is leaked.
After years of IPv6 use, I have seen no practical difference between IPv6 and IPv4 for day-to-day browsing. So we can sacrifice IPv6 for outbound traffic and reserve it solely for “go home” access.
How to block AAAA records
Configure your internal DNS resolver to drop all AAAA answers.
Most home setups run AdGuard Home—see the screenshot:
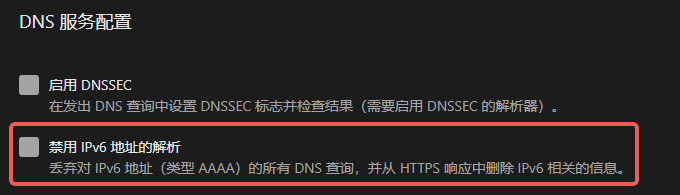
Once applied, local devices reach the outside world over IPv4 only.
Never Expose Services by IP
Exposing a service on a naked port makes discovery trivial. When you start a service, avoid binding to 0.0.0.0 and ::; almost every tutorial defaults to 127.0.0.1 plus ::1 for good reason—listening on public addresses is risky.
Reverse-proxy only by domain name
nginx example
Set server_name to an actual hostname instead of _ or an IP.
server {
listen 80;
server_name yourdomain.com; # replace with your real domain
# 403 for anything not the correct hostname
if ($host != 'yourdomain.com') {
return 403;
}
location / {
root /path/to/your/web/root;
index index.html index.htm;
}
# additional config...
}
IIS example
Remember to specify the exact hostname—never leave the host field blank.
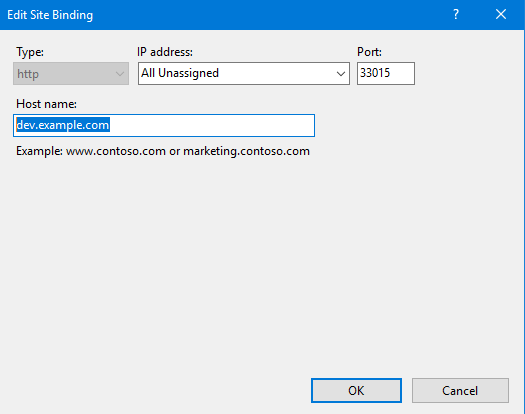
Use a private DNS service
Create spoofed hostnames that resolve only inside your own DNS.
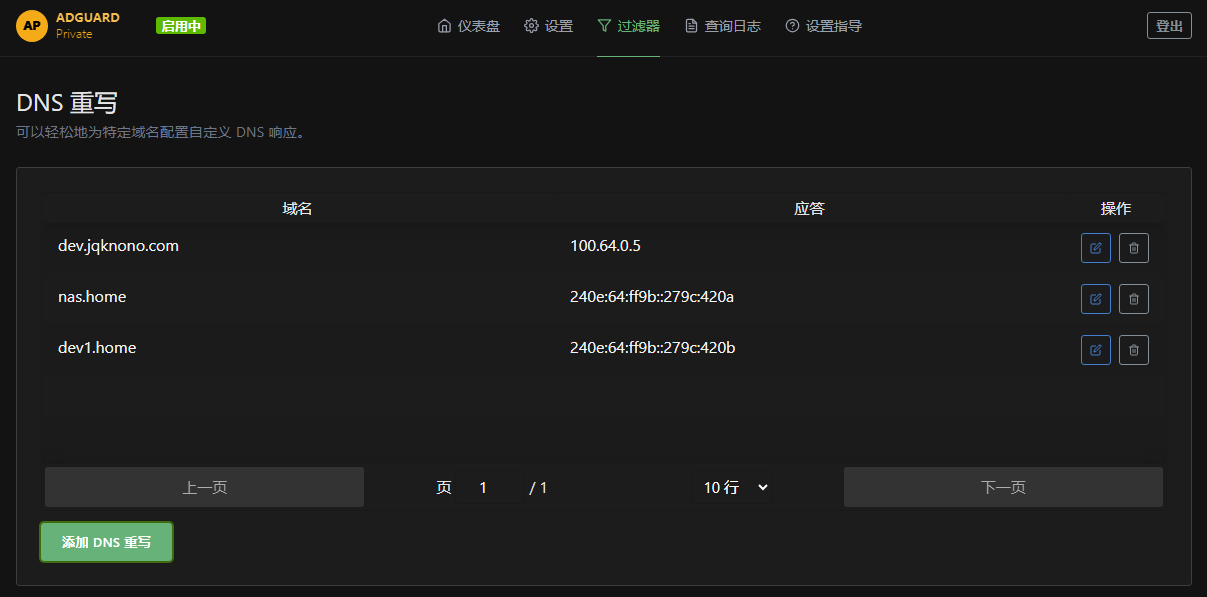
Benefits:
- Hostnames can be anything—no need to buy a public domain.
- If a fake hostname leaks, the attacker still has to point their DNS resolver at your private server.
- Scanning the IP alone is useless: one must also (a) know the fake name, (b) set their resolver to your DNS, (c) include that name in each request’s Host header. All steps have to succeed.
sequenceDiagram
participant Scanner as Scanner
participant DNS as Private DNS
participant Service as Internal Service
Scanner->>DNS: 1. Find private DNS address
Scanner->>DNS: 2. Query fake hostname
DNS-->>Scanner: 3. Return internal IP
Scanner->>Service: 4. Construct Host header
Note right of Service: Denied if Host ≠ fake hostname
alt Correct Host
Service-->>Scanner: 5a. Response
else Wrong Host
Service-->>Scanner: 5b. 403
end
This significantly increases the scanning cost.
You can deploy AdGuardPrivate (almost a labeled AdGuard Home) or Tencent’s dnspod purely for custom records. Functionality differs, so evaluate accordingly.
Summary
-
Prevent the internal DNS from returning AAAA records
- Pre-reqs
- Public IPv6 prefix
- Internal DNS resolver
- Steps
- Drop AAAA answers
- Pre-reqs
-
Reach internal services only via domain names
- Pre-reqs
- You own a domain
- Registrar supports DDNS
- Local reverse proxy already running
- Steps
- Enable DDNS task
- Host-based access only
- Pre-reqs
-
Spin up a private DNS
- Pre-reqs
- Private DNS service with custom records and DDNS
- Steps
- Enable DDNS task
- Map fake hostnames to internal services
- Pre-reqs
Finally:
- Tailscale/Zerotier that successfully punch through are still the simplest and safest way to go home.
- Don’t hop on random Wi-Fi—you’ll give everything away in one shot. Grab a big-data SIM and keep your faith with the carrier for now. (Cheap high-traffic SIM? DM me. Not really.)