How a vendor bypasses DNS blocking
Recently I noticed that the DNS public service IP is receiving abnormal traffic—tens of identical requests for the same domain every second, completely ignoring the DNS protocol and the global TTL value.
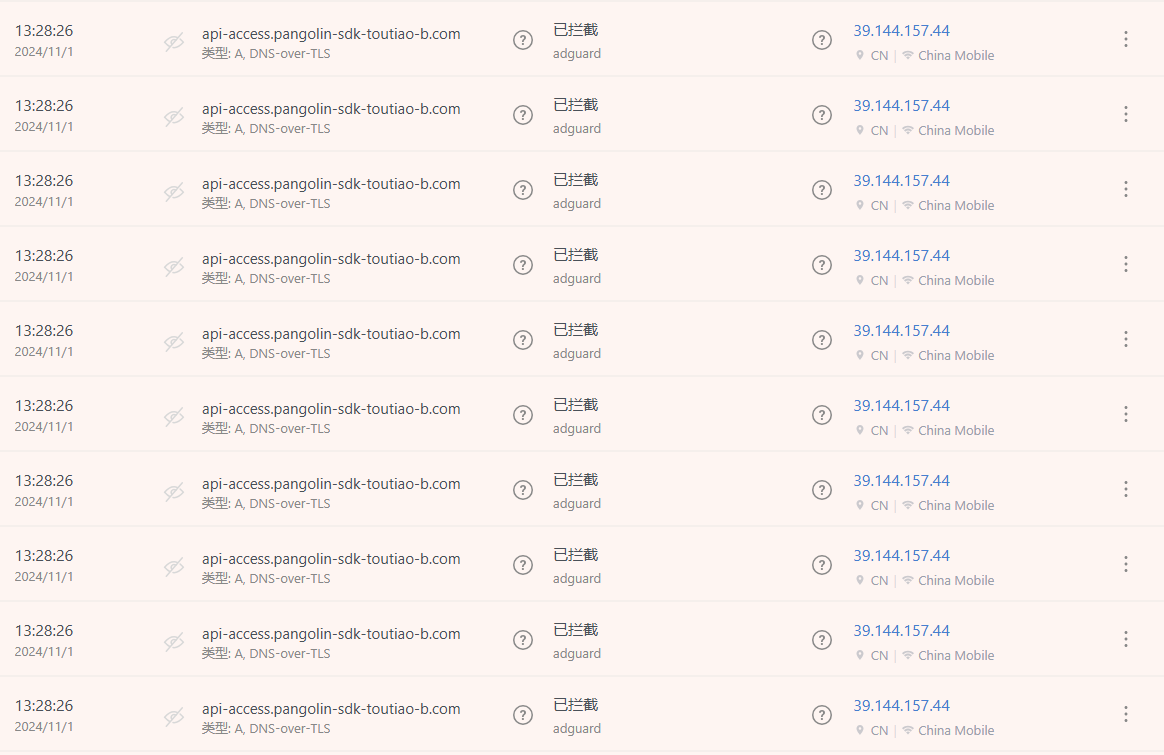
At first I thought the IP belonged to an attacker, but inspecting the flows revealed it was simply a certain vendor’s App frantically querying DNS. The backend sets TTL=10, meaning any client that has just received the DNS response should cache it for ten seconds instead of re-querying the DNS server. Yet the App pounds the server with dozens of identical requests every second, proving it never honors the TTL. In our blocking statistics, more than 90 % of intercepted requests are for this single domain.
Perhaps the vendor knows DNS queries can be blocked and therefore sends its Apps to launch a direct DoS on your DNS resolver—its way of saying “If you don’t let me through, I’ll drown you.” Since the backend also has a cap of 20 burst queries per second, this reckless behavior impedes other normal DNS queries from the same user, disturbing other Apps.
The ops team, facing relentless queries for one domain from a single IP, ends up whitelisting it even when they’d rather not.